
Phishing remains a dominant factor in cybersecurity. It’s the #1 delivery method for ransomware, viruses, and other types of malware as well as the main cause of data breaches.
The art of phishing has come a long way since the days of long rambling, misspelled emails. Today’s phishing attacks are personal, hard to detect, and often use the logo and signatures of well-known companies.
In this article, we’ll go through the common types of phishing tactics you need to watch out for as well as how to spot a phishing attack. This is a great article to share with employees to help them increase their phishing and IT security awareness.
What to Watch Out For | Common Phishing Attacks
There are multiple attack types and strategies used by phishing scammers, we’ll go over the most common to watch out for below.
Purchase Orders
Who doesn’t get excited when someone wants to buy something from your company? The promise of a good size purchase order is all that some people need to encourage them to open an email, even if it’s from a company they’ve never heard of.
But sending fake purchase orders is a common phishing tactic. Emails will typically mention a large dollar amount that they’d like to purchase and include an attachment.
Once opened, the attachment typically unleashes malware into a device. Excel is used often because it tends to be a trusted file type, But, using macro scripts, Excel files can release malware.
Spoofed Emails
A common tactic used in phishing to get a user to trust an email is to put a domain name they know in the “From” line. This won’t be who the email was actually sent from, but many users don’t know this.
Seeing [email protected] can often fool employees into believing a phishing email is legitimate.
Between 2019 and 2020, 88% of surveyed businesses experienced phishing attacks using spoofed emails.
Looking at the “From” line is not enough to tell a real email from a fake because the email can be spoofed.
Order Receipts & Tracking
Two types of emails that users are used to seeing in their inboxes are order receipts and tracking notices. That’s why these are often used in email phishing attacks.
Users see an invoice receipt or tracking notice from what looks like a legitimate source and clicks a link to review the order that they don’t remember. This type of email typically takes them to a spoofed login page and is designed to steal credentials.
Sharing Links to Microsoft Office Documents
One of the newer tactics that phishing attacks have been using is to send an email that looks like a SharePoint or OneDrive file sharing link.
Users will tend to trust the document type they see in the URL and click the link. One thing that can happen is that when the file is opened it redirects the user to a malicious site. Another tactic is a fake Microsoft 365 login page.
This tactic is also used for non-Microsoft links, such as Dropbox files.
How to Identify a Fake Email
It’s increasingly difficult to tell fake emails from real ones. However, there are certain telltale signs as well as solid tactics you can use to avoid becoming a phishing victim.
Hover Over Links (Don’t Click!)
Phishing emails will often hide links behind manipulated text or images, but you can reveal a real link without clicking on it. Hover over links with your cursor and the real URL will pop up. This often reveals a phishing scam.
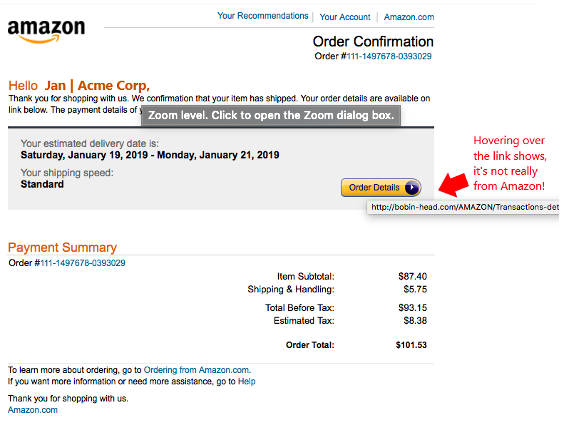
View the Email Header Source Code
When you have your email open in a program like Outlook, you can click to view the source code of the message. You want to look at the header for the mail path, this will reveal the true email address than sent the message.
Using this method, you can often identify if an email has been spoofed because the source code will show another email address in the return path.
Suspect Anything You Weren’t Expecting
It’s a good best practice to be suspicious of any type of email that you weren’t expecting, even if it looks like it comes from someone you know.
If you receive an employee survey from HR that you weren’t expecting, call your HR department to confirm. The same goes for any unsuspected emails, especially those that have a link or an attachment.
Look for Anything That’s “Off”
Phishing scammers have gotten better with grammar and spelling when sending phishing, but sometimes you can still find one if you look hard enough.
Carefully review unexpected emails for any slight grammar mistakes, misspelled words, or something else that’s slightly “off” about a reference it makes.
Keep Phishing at Bay With Solid Cybersecurity Solutions
Data First Solutions offers email protection and other cybersecurity solutions that can protect your GTA business from phishing and other types of attacks.
Contact us today to book a free assessment. Call 416-412-0576 or book your assessment online.










You must be logged in to post a comment.